Executive Summary
If you're a startup founder, "Anti-Money Laundering (AML) compliance" probably sounds like a huge, expensive, corporate headache you can (and should) deal with way later, right? Here’s the thing: it’s not. In today's world, AML compliance is an "everyone" problem, and it's one of the first, most serious hurdles you'll face as you start to get real traction. The moment your company handles money, you become a gatekeeper—and a target. Ignoring it is like building a skyscraper with no fire escapes: everything's fine until it's not, and then it's catastrophic. But here's the good news: you don't need a 2,000-person compliance team. You just need a smart plan. This isn't a boring legal textbook. This is a practical, step-by-step playbook for founders and operators. We're skipping the "why" (mostly) and jumping straight to the "how." How to figure out your actual risks, what to write in your first AML policy, how to use modern tools (like automated sanctions screening) to do the heavy lifting, and how to build a program that VCs and banking partners will love because it shows you're building a real, sustainable business. Let's build a simple, scalable AML program that actually helps you grow.
Introduction: Why "Waiting to See" Is a Failed Strategy
In the early days, you're all about product, growth, and just plain survival. "Compliance" gets tossed on the "someday/maybe" pile. But that's a massive strategic mistake. In today's ecosystem, your AML setup isn't just for the government (who will, eventually, catch up). It's for the partners you need right now to even exist.
Payment Processors (Stripe, Adyen, etc.): They are heavily regulated. They are on the hook for the risks you bring to their platform. They will not risk their licenses to partner with a platform that has a messy or non-existent compliance program. They'll shut you down first and ask questions later. A sudden freeze on your payment processing can kill your cash flow and your company overnight.
Banking Partners: You want a real business bank account? The first thing they'll ask for is your AML policy. No policy? No bank account. It's often a relationship-ender before it even begins, forcing you into less-desirable, high-fee banking options that stifle your growth.
Investors (VCs): Gone are the days of "growth at all costs." Especially post-Series A, investors do serious due diligence. A messy compliance program is a giant, flashing red light that screams "hidden liabilities" and "operational chaos." To them, it means future fines, frozen accounts, and emergency "clean-up" projects that will kill your product roadmap and burn their cash.
"We look at two things: the product and the risk. A great product with messy compliance is a risk we won't take. A good product with a clean, automated compliance program? That's a mature, scalable business. We'll fund that one all day."
The goal isn't to become a bank. The goal is to build a smart, risk-based, and auditable program that fits your size. This guide shows you exactly how.
Chapter 1: The Foundation — Your AML Risk Check-Up
Okay, first things first. You can't build a smart plan if you don't know what you're up against. This is what regulators mean by a "risk-based approach." It's just a fancy way of saying: "Focus your energy where the real danger is." Before you write a single line of your policy, you need to do a quick "Risk Check-Up" for your business. This can (and should) be a simple internal document. Grab your co-founder and a whiteboard. You're going to analyze three key areas.
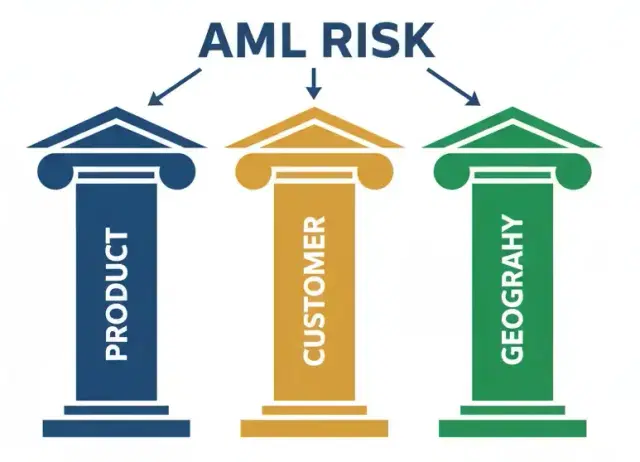
1. Product & Service Risk ***What is it about your product that a money launderer
might find... useful?***
High Risk: Holding People's Money: Are you a digital wallet? A marketplace that holds funds in escrow? A platform that lets users "cash in" and "cash out"? Anytime you are a "custodian" of funds, your risk shoots up. Moving Money (Especially Cross-Border): Are you a fintech, a remittance app, or a payments company? The faster and more global the movement, the higher the risk. A launderer's goal is to move money far and fast to obscure its origin. Anonymity: Does your platform allow anonymous or pseudonymous accounts? (This is why crypto exchanges are in the high-risk spotlight). Anything that hides the "who" is a red flag. Complex Products: Are you in gaming (virtual goods that can be traded for real money), digital assets (NFTs), peer-to-peer (P2P) lending, or anything that can obscure the source of funds?
Low Risk: Simple B2B SaaS: You sell a $50/month subscription for a software tool that doesn't touch your clients' money. E-commerce: You sell physical goods (like T-shirts or coffee) directly to consumers. (Note: You still have sanctions risk! You can't ship a T-shirt to a sanctioned person). Informational Services: A B2B insights platform where clients just pay a subscription to read content.
2. Customer Risk
Who are your customers, and what do they really do?
High Risk: Politically Exposed Persons (PEPs): Government officials, their families, and their close associates. They aren't criminals, but they are high-risk because they have more opportunities for bribery and corruption. Cash-Intensive Businesses: Restaurants, convenience stores, car washes, etc., that you might be servicing with a new POS system. Unknown Entities: Customers who are "shell companies," trusts with unclear owners, or a B.V.I. company with a "nominee" director. Basically, anyone hiding who really owns the account. Customers Who Don't Make Sense: Why is a user from a country you don't serve trying to move $100,000 through your small app? Why is a "t-shirt company" suddenly receiving $500k in payments from a high-risk jurisdiction? Red flag!
Low Risk: Regular people (the general public) making small, predictable domestic payments (e.g., paying for their coffee). Well-known B2B companies in regulated industries (e.g., selling your SaaS to another well-known, publicly-traded tech company).
3. Geographic Risk
Where are your customers, and where is the money going to (or coming from)?
High Risk (Sanctioned): These are the "no-go" zones. Doing any business with individuals or entities in countries like North Korea, Iran, Syria, Cuba, and the occupied regions of Ukraine is illegal and will get you shut down. This also includes nationals of these countries, even if they live elsewhere. The penalties are "strict liability," meaning "I didn't know" is not a legal defense.
High Risk (Jurisdictional): These are countries that the rest of the world has "grey-listed" for having weak AML controls. The global watchdog, the Financial Action Task Force (FATF), keeps a public list. You can do business here, but you need to be extra careful. This also includes "banking secrecy" havens.
Low Risk: Operating entirely within one, well-regulated country (e.g., just in the US, just in the UK).
- Schedule a 1-hour "Risk Workshop" with your founding team. - Create a simple spreadsheet with three tabs: Product, Customer, Geography. - For each tab, list your risks and rate them "Low," "Medium," or "High." - Write a one-paragraph summary: "Our primary risks are [e.g., anonymous crypto users] and [e.g., cross-border payments]." - Save this document. This is v1.0 of your official Risk Assessment. Congrats!
Chapter 2: The Blueprint — Your Core AML Policy
Now that you know your risks, you can write your "rulebook." This is your AML Policy. Think of this as the "constitution" for your compliance program. It's the first document a bank or investor will ask to see. It doesn't need to be 100 pages, but it must have these sections.
What to Put in Your Startup's AML Policy (v1.0):
1. Policy Statement (The "Promise"):
- A high-level paragraph from you (the founder/CEO) stating, "We are 100% committed to preventing financial crime on our platform. We take this seriously." This isn't just fluff; it's your "tone from the top," which auditors look for.
2. "Point Person" (Your MLRO):
- Name the one person who is ultimately responsible for this program. (We'll cover this in the next chapter). Give their name and title (e.g., "Jane Doe, COO, is our designated Money Laundering Reporting Officer (MLRO)"). This centralizes responsibility, preventing the "it's not my job" problem.
3. (The "Why"): State that you use a "risk-based approach."
- State that you use a "risk-based approach."
- Include a short summary of your Risk Check-Up. (e.g., "Our assessment identified high risks in cross-border transactions and user anonymity..."). This section proves your policy isn't one-size-fits-all, but tailored to your business.
4. Customer Due Diligence (CDD) / Know Your Customer (KYC):
- When you do it: e.g., "We will identify and verify all users at onboarding, before they can access financial features."
- What you collect: e.g., "For all users, we collect legal name, date of birth, and residential address. For high-risk users, we also collect a government-issued ID."
- How you check: e.g., "We verify this information using a combination of documentary (ID) and non-documentary (database) methods via our third-party technology partners." This section details your 'front door' policy: who you let in and how you check their ID.
5. Sanctions & PEP Screening (The "Shield"):
- Which lists you check: Be specific! "We screen all users against, at a minimum, the sanctions lists issued by the U.S. Office of Foreign Assets Control (OFAC), the United Nations (UN), the European Union (EU), and the UK (HMT)."
- When you check: "Screening is performed automatically via API at onboarding. Our entire customer base is re-screened daily to catch any new updates to these lists." This is your non-negotiable shield. It details how you stop 'bad actors' before they're in your system.
6. Transaction Monitoring (The "Alarm System"):
- How you watch: "We monitor transactions for suspicious activity using a mix of automated rules and manual, risk-based reviews."
- Your "Red Flags": List 5-10 red flags specific to your business.See more in Chapter 3. If KYC is the front door, this is the alarm system inside the house.
7. Reporting Sketchy Stuff (SARs):
- Internal Process: Explain how an employee tells the "Point Person" they saw something weird.
- External Filing: State that the Point Person is responsible for investigating and, if necessary, filing a Suspicious Activity Report (SAR) with the relevant government body (e.g., FinCEN in the US, NCA in the UK). This explains your 'duty to report'—what you do when you find something genuinely suspicious.
8. Team Training (The "How-To"):
- Who: "All employees will receive AML training, with specialized, role-based training for engineering, support, and operations."
- When: "Training is provided at hiring and on an annual basis." This ensures the policy isn't just a document, but a living practice within the company.
9. Record Keeping (The "Proof"):
- What you keep: "We keep all KYC data, screening results, transaction logs, and investigation notes."
- How long: "All records will be kept for a minimum of five years after the business relationship with the customer ends." This is your 'audit trail'—the proof that you're doing everything you said you would.
This is not legal advice! This playbook is a comprehensive guide, but it's not a substitute for a real lawyer. Use this to build your program, and then have a qualified legal professional review it.
Chapter 3: The 5 Pillars of Your AML Program
Alright, let's actually build this thing, pillar by pillar.
Pillar 1: The "Point Person" (Your Owner/MLRO)
You must designate one person who is ultimately responsible. In a startup, this is almost never a full-time "compliance officer."
- Who: It's usually the COO, Head of Operations, Head of Finance, or a Co-Founder.
- What makes a good one? They need to be organized, skeptical (in a good way!), analytical and detail-oriented, and have enough authority to tell other teams (even product!) "no, we can't launch that yet." This authority is non-negotiable; they must be able to enforce the policy.
- Own and update the AML Policy.
- Oversee the tech partners (your KYC and sanctions tools).
- Personally review the "big" alerts (a real PEP match, a $500k weird transaction).
- File the official SARs with the government.
- Run the annual team training.
- Act as the single point of contact for all regulatory and banking partner inquiries.
Pillar 2: Customer Due Diligence (KYC / CDD)
This is just a fancy way of saying "know who you're dealing with." It's not one single thing; it's a ladder of steps.
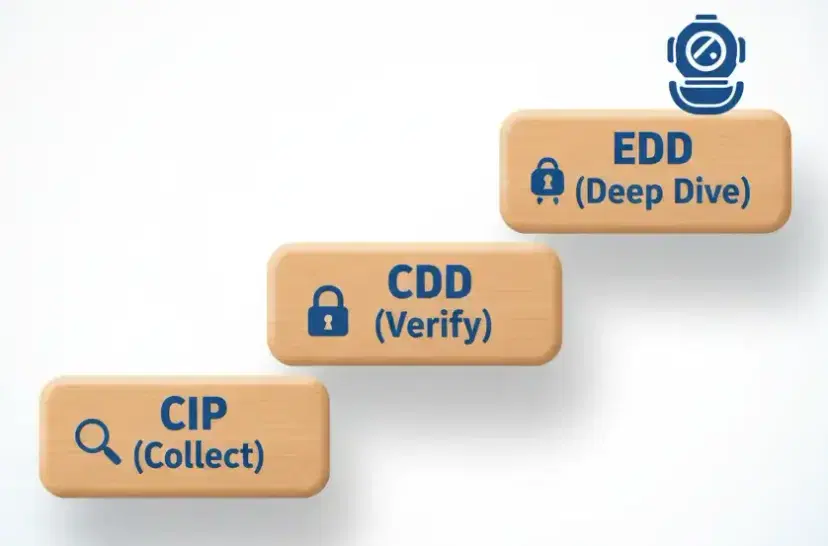
-
Step 1: CIP (Customer Identification Program)
- What it is: Just collecting the basic info. This is your user's sign_up_form.js. This is the minimum data you need to even begin a check.
- Info: Legal Name, Date of Birth, Address, Government ID Number (like a SSN or equivalent).
-
Step 2: CDD (Customer Due Diligence)
- What it is: Proving the info is real. This is where you move from "collecting" to "verifying."
- How: You partner with a tech provider to do this.
- Documentary: The user uploads a photo of their passport or driver's license. The tool uses AI to see if it's real.
- Non-Documentary: The tool pings databases (credit bureaus, government records) to see if "Jane Doe, born 1/1/1990 at 123 Main St" is a real, live person. Using both (e.g., matching a passport photo to a database record) creates a much stronger verification than either one alone.
-
Step 3: EDD (Enhanced Due Diligence)
- What it is: This is the "deep dive" you do for your highest risk customers (like a PEP you've confirmed, or a user wanting to move $5M).
- How: You have to ask more questions, like "Where did this money come from?" (Source of Funds) and "What's the source of your total wealth?" (Source of Wealth). This could also involve "adverse media" screening—checking news sources to see if they're linked to fraud, bribery, or other crimes. This is usually a manual process.
Don't build this yourself! Partner with a third-party "Identity Verification" (IDV) tool. It's cheaper, faster, and infinitely more secure.
Pillar 3: Sanctions & PEP Screening (Your Automated Shield)
This is your single most important, can't-skip-it, non-negotiable control. It is illegal to do business with a person or company on a sanctions list. The fines are massive.
What’s a Sanction?
A “block list” issued by a government. If a person, company, or country appears on it, you cannot do business with them.
The main lists are OFAC (US), EU, UN, and UK (HMT) — together they form the global baseline for compliance.
What’s a PEP?
A Politically Exposed Person. They are not criminals by default but are high-risk because of exposure to corruption or bribery.
Examples include government ministers, state governors, senior military officials, and their immediate families.
You can work with them, but you must apply Enhanced Due Diligence (EDD) from Step 3.
Why You Must Automate This
- Lists change daily: OFAC alone can add or update dozens of names in one day. Manual updates are impossible.
- Fuzzy matching is complex: “Mohamed Al-Fayed” vs. “Muhammed el Fayed.” A proper screening engine handles transliteration, spelling, and cultural variations.
- Manual searches are invalid: Googling users is not auditable or defensible. Regulators require timestamped proof of every screening event.
Do not build this yourself. Maintaining and normalizing dozens of global watchlists is a full-time data engineering task. Use a dedicated API service for automated, real-time sanctions and PEP screening.
How to Implement It (The "How-To")
At Onboarding
When a user signs up, your backend should trigger a quick API call to your screening provider (for example, POST /v1/screen_user).
If the response is a hit, stop the onboarding or place the user in a pending review state.
This is your gate — no one enters until cleared.
Perpetual (Ongoing) Screening
This part is critical. Your screening partner must re-screen your entire customer base daily against updated sanctions and PEP lists.
A user who is clean on Monday can appear on a sanctions list by Tuesday.
You need to know the moment it happens, not at their next login.
Daily, automated re-screening protects your business from retroactive risk. Compliance is not a one-time check — it’s a continuous process.
Pillar 4: Transaction Monitoring (Your Alarm System)
This is how you detect suspicious activity after a user is in your system.
You’re watching for behavior that doesn’t make sense.
Startup Tip:
You don’t need a million-dollar AI platform on Day 1.
Start with a few simple, automated rules that trigger alerts for your Point Person to review.
- Threshold: Alert on any transaction over a set amount (for example, $10 000). - Structuring: Alert on multiple transactions just below that threshold (for example, five × $2 000 in 24 hours). - Velocity: Alert on a user with an unusually high number of transactions in a short period. - In-and-Out: Alert on a deposit of $50 000 followed by a $49 900 withdrawal an hour later — classic “layering.” - Geography: Alert on any transaction touching a high-risk country from your FATF grey list. - Time-of-Day: Alert on users active only at 3 AM — possible bot or compromised account. - Impossible Travel: Alert on a user logging in from New York and 20 minutes later from Moscow. - New-Account Max-Out: Alert on brand-new accounts that instantly move the maximum-allowed amount. - Multiple Sources: Alert on accounts receiving many small payments from 50 new sources, then consolidating them. - Sanctioned Crypto Wallet: Alert on any crypto transaction touching an OFAC-listed wallet address.
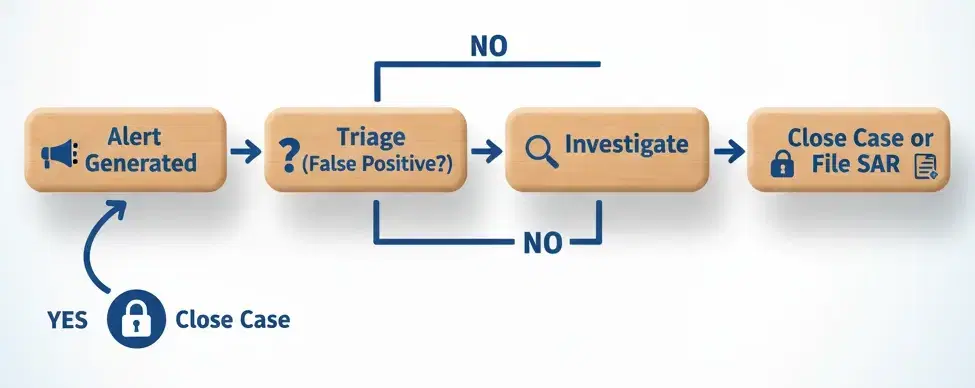
Automate alerts, but review them manually. The goal is not volume — it’s precision and a clear, auditable record of decisions.
Pillar 5: Reporting (SARs)
When your alarm system flags something you can’t explain — it’s not a false positive, and the story doesn’t add up — you have a legal duty to report it.
What It Is
A Suspicious Activity Report (SAR) is a standardized, confidential report filed with your country’s Financial Intelligence Unit (FIU).
Filing a SAR does not mean the user is guilty; it means you have a reasonable suspicion and are passing that information to authorities.
The Golden Rule
NO TIPPING OFF! This is the single most important rule in AML. You must never — under any circumstance — tell a customer or anyone else that you are filing a SAR on them. Doing so is a criminal offense. It can compromise investigations and allow suspects to destroy evidence or flee. Your only action is to file the report and, if appropriate, quietly offboard the customer.
Chapter 4: The "Glue" — Training & Record-Keeping
These last two pillars aren’t “action” steps, but they’re the glue that keeps your AML program auditable and defensible.
If you’re ever audited, this is how you prove you did everything described in Chapter 3.
1. Employee Training
If your team — especially Support — doesn’t know what to look for, your program fails.
Who: Everyone needs at least a basic “AML 101” session.
Specialized: Engineering, product, and support teams require deeper, role-specific training.
- Support: Train them to recognize social engineering and handle sensitive customer inquiries like “Why was my $50k transfer flagged?”
- Engineering/Product: Teach them that AML depends on strong data privacy and secure design. They handle highly sensitive personal data and must treat it accordingly.
- What is AML & Terrorist Financing? (10 min) - Review of the company AML Policy (15 min) - Key Red Flags (10 min) - The “Alert” Process — what to do if you see something (10 min) - The “No Tipping Off” Rule (5 min) - Q&A (10 min)
How:
Run this training live during onboarding and record a refresher for annual review.
Maintain a training attendance log — auditors will request it as evidence of compliance.
An AML program is only as strong as the people running it. Training creates awareness, consistency, and a documented proof of control.
2. Record-Keeping
If you didn’t write it down, it didn’t happen.
In an audit, your records are your only defense.
- Results of all KYC/IDV checks (pass or fail). - Screenshots or logs of every sanctions and PEP screening result — especially “hits” — and your notes on why you cleared or escalated them. - All transaction logs. - All investigation notes for every transaction alert. - Copies of all SARs you filed. - Annual training decks and attendance logs. - All historical versions of your AML Policy and Risk Assessment — this shows how your program evolved.
How Long:
Keep all records for at least five years after a customer closes their account.
This retention period is a standard global requirement.
Strong record-keeping transforms your AML program from words on paper into defensible evidence of compliance.
Chapter 5: Building Your AML Program by Stage
Your compliance program should scale with your company.
Here’s what to focus on at each growth stage.
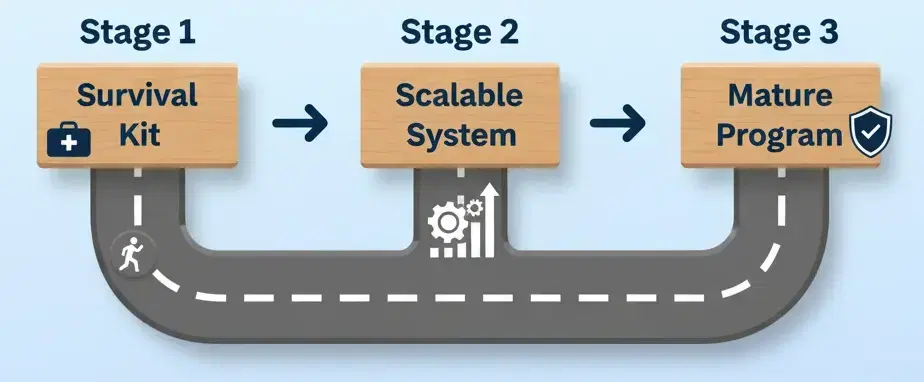
Stage 1: The "Survival Kit"
Company Status: Pre-Seed / Seed (Building Product, 0–10k users)
- Appoint Owner: A Co-founder (e.g., COO) acts as the Point Person. - Risk Assessment: Complete the 1-hour Risk Check-Up (see Chapter 1). - AML Policy: Draft your v1.0 AML Policy (see Chapter 2). - Integrate Sanctions API: Top priority — set up automated sanctions and PEP screening at onboarding. This is your Minimum Viable Compliance.
Stage 2: The "Scalable System"
Company Status: Series A / B (Growth, 10k–500k users)
- Dedicated Resource: Hire your first junior or mid-level Compliance Ops person under the Point Person to manage daily alerts. - Full KYC: Integrate a third-party ID verification (IDV) provider. - Transaction Monitoring: Implement 5–10 automated rules (see Chapter 3, Pillar 4). - Training: Roll out your first formal, annual, recorded AML training.
Stage 3: The "Mature Program"
Company Status: Series C+ (Scaling, 500k+ users)
- Hire a Leader: Appoint a dedicated senior Head of Compliance or MLRO. - Automate Monitoring: Deploy a formal automated transaction monitoring system — this is where AI in AML becomes valuable. - Get Audited: Hire an independent third party to audit your program before a regulator does. - Refine Policy: Update your AML Policy to v3.0, and refresh it with every new product or market entry.
Compliance maturity mirrors product maturity. Start simple, automate early, and evolve your program as your risk surface grows.
Chapter 6: The Tech Stack (Build vs. Buy)
At Stage 1, every founder faces the same question:
“Can’t our engineers just build this?”
The 'We'll Build It' Fallacy: A Cautionary Tale
PaySwift, a fictional but realistic startup, decided to build its own sanctions screener.
“How hard can it be?” the technical founder said. “It’s just matching names against a list.”
Month 1: They downloaded the OFAC list. Easy.
Month 2: They discovered the EU, UN, and UK lists all came in different formats — XML, CSV, TXT — requiring custom parsers for each.
Month 3: They launched. Their exact-match system missed Mohamed Al-Fayed because the list said Muhammed el Fayed.
Month 4: An update to the OFAC list broke their parser. It went unnoticed for 72 hours, during which they onboarded three sanctioned users.
Month 6: Their banking partner did a spot check, found the sanctioned users, and froze their account.
Not to mention:
different alphabets for the same name,
the need to link and normalize associated entities to sanctions,
structuring and standardizing data from multiple sources (birth year, nationality, birthplace),
and parsing complex identifiers such as passport numbers or tax IDs.
PaySwift spent six months and thousands of engineering hours to build a system that was slow, inaccurate, and ultimately non-compliant.
A dedicated API-based screening solution could have been integrated in one afternoon, cost less than a single month of engineering time, and delivered real-time, fuzzy-matched, continuously updated results.
Engineering resources are best spent building your product — not rebuilding compliance infrastructure. Buy what scales, build what differentiates.
Conclusion: From Compliance Burden to Growth Engine
AML compliance isn’t just a legal checkbox — it’s a signal of trust, maturity, and operational excellence.
Startups and scale-ups that treat compliance as a growth enabler, not a distraction, gain access to better banking partners, faster investor confidence, and smoother international expansion.
The modern approach is simple:
- Automate what machines do best — screening, monitoring, and record-keeping.
- Keep humans focused on judgment, oversight, and transparency.
- Document everything, train everyone, and audit yourself before someone else does.
You don’t need a 50-person compliance department to stay compliant — you need clarity, automation, and accountability.
That’s how high-growth companies build programs that scale with them, not against them.
“The strongest compliance programs don’t slow innovation — they make it safe to grow.”